A technical organization’s value and survival lie in its Intellectual Property (IP). Everything today is about information, and the rapid advancement in technology has made accessing and distributing such information much easier. As such, it is now harder to safeguard your IP from theft and copying.
Taking the proper steps to protect your IP should be a priority for your business regardless of whether you’re a start-up or a vast conglomerate.
Table of Contents
What Is Intellectual Property?
Intellectual property is an intangible asset of the original thought. It is an asset your company owns that gives it the edge and a competitive advantage in the marketplace. Simply put, IP refers to any unique asset that you use as part of your business or its operations.
The World Intellectual Property Organization sees IP as creations of the mind. It can cover a massive range of assets, including artwork, designs, your website content, blog posts, articles, manuscripts, inventions, business names, product names, software, programs, or other original information that benefits your business.
IP rights are usually granted to the creators of the original works that are the result of human intellectual creativity. Some types are automatically safeguarded by law from the moment of their creation, such as copyright. At the same time, some require respective government agencies to grant specific rights before being protected by law.
The four legally defined IP categories you can prosecute for theft are:
- Patents (lasts for 20 years) – once you have the legal right for your software, others cannot manufacture or market your software. However, they can apply to license your product.
- Trademarks (lasts for ten years) – refer to names, phrases, symbols, even sounds used with services or products. That is essential for any brand with a level of quality on which companies build a reputation.
- Copyright (lasts for the life of the author + another 50 years) – used to protect written or artistic expressions in a tangible medium (songs, poems, novels, or movies). Bear in mind that copyright doesn’t cover the idea itself but only the expression of an idea. Although you don’t need to register your material to hold a copyright, registration is necessary if you decide to sue for copyright infringement or send cease and desist letters.
- Trade secrets – covers a specific formula, pattern, device, or data that grants the user an advantage over competitors. This category is covered under state laws rather than federal. A business must prove that it adds value to the company, that it is an important secret, and that appropriate measures have been taken to safeguard the secret, and that appropriate measures, including compliance with data privacy laws, have been taken to safeguard this invaluable asset, ensuring both legal protection and confidentiality.
Why Safeguarding Your Intellectual Property Is Important
A survey of 53 countries in 2023 revealed the top 19 countries with the best intellectual property environments. The leading country was the United States, with a strong overall score of 95.48 points. They measured based on several key indicators, namely patents, copyrights, trademarks, enforcement, membership, and ratification of international treaties.
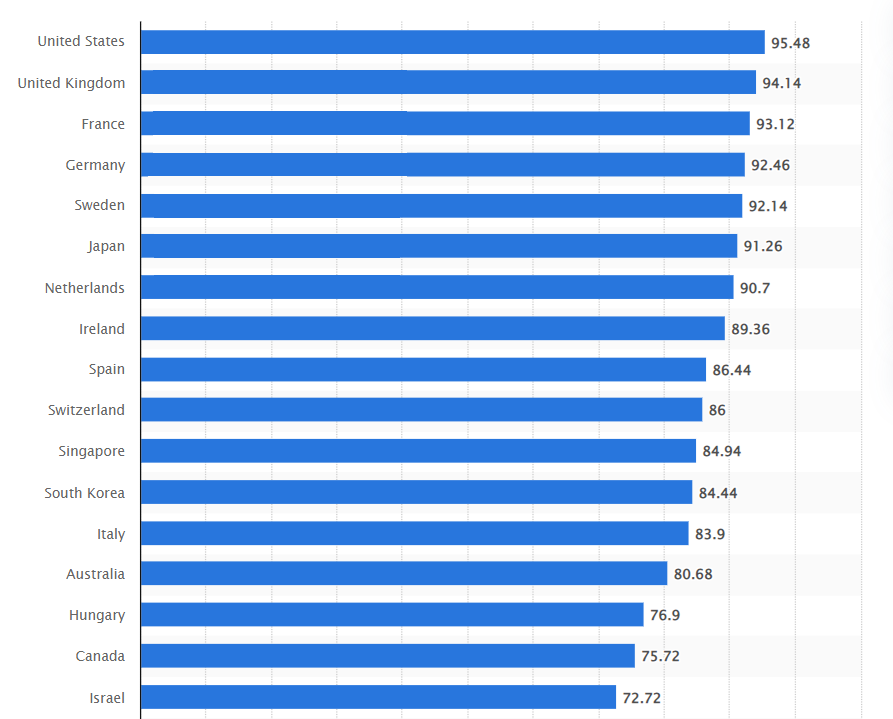
That shows that the adoption of IP protection has already gained strong momentum in many countries, showing greater awareness regarding the importance of safeguarding their IPs.
Bear in mind that protecting your IP is critical to fostering innovation. If you don’t protect the IP of your products, businesses will not be able to reap the full benefits of their inventions. Also, safeguarding your IP is crucial to provide an important revenue stream and helps set your business apart from its competitors. That is what gives you the needed competitive edge.
5 Ways to Protect Your Software Intellectual Property
Developing a highly valuable product for your business can take great minds a significant amount of time and effort. The last thing you’d want for your company is another company stealing your ideas. However, once open to the public, IP can easily be copied.
Remember, IP is the lifeblood of every organization. As such, you have to give serious thought to safeguarding the IP of your software. Under US law, there are the following ways that you can protect your IP.
File for Copyrights, Trademarks, and Patents
Copyrights (©)
The US copyright office defines copyright as legally enforceable protection for original work or production. The same law also protects original software since the code is seen as an authored product. The protection applies as soon as the items are created.
In addition to this natural protection, the office also recommends that any such production be registered with the office. In this process, firmer legal recognition may help boost the capabilities of legal enforcement if it should be necessary.
Take note that the US has copyright relations with most countries throughout the world. As such, once you’ve registered your software with the US, this is also upheld in other countries. That said, you can check the listing of countries and the nature of their copyright relations with the US to confirm further.
Upon successfully registering your copyright, this means that you have claimed legal copyright protection for your software. As such, you can sue anyone who infringes upon your copyright, using your intellectual information for gain without your permission.
You can use the Web Hosting Secret Revealed Tool to help you trace and gather the technical details behind the culprit’s website/app origins. Then, you can officially file a complaint to the respective web hosting to take down the website/app (e.g. DMCA complaint).
Trademarks (™)
The US defines a trademark as a way to protect words, phrases, symbols, or designs identifying the source of the goods or services of one company and distinguishing them from those of others. Businesses use such symbols, designs, and catchphrases as part of their marketing strategy and to build identity.
These are important to a company as they are used to connect to its customers. As a result, they need to be protected from possible commercial saboteurs who might use them for their economic gain.
You can register your trademark online with the US Patent and Trademark Office (USPTO) in the US. You’d need a trademark lawyer to help you with this as the whole process can be rather tedious and extensive.
Generally speaking, trademarks do not have expiration dates since you own the rights to them in perpetuity. However, it’s advisable to file for a Section Eight declaration to confirm that the IP is still active and in use.
Patents (®)
If your software has a unique feature or design that separates it from your competition, you should protect your competitive advantage with a patent. A patent legally protects inventions or discoveries, thus preventing others from making and distributing your invention unless you’ve given them the license to do so.
If you wish to protect the IP of your software design, you can file for a patent with USPTO online. Bear in mind that there are different types of patent processes; the respective related conditions or requirements depend on the invention, so you’ll need to know which applies best to your software before proceeding.
In the US, most IP patents have validity from 15 to 20 years after the filing date, after which you’ll have a patent-pending status unless you renew with the USPTO.
Sign Confidentiality or Licensing Contracts with Employees and Partners
When you’re developing software, it is always a good practice to protect it from the get-go. You do so by getting the developers, all relevant personnel involved, and even partners to sign a confidentiality agreement to ensure IP protection.
Lawyers and bound employees and workers must prepare such agreements to comply with the necessary to protect what is private. Otherwise, they will not be legally liable for any leaks. Confidentiality agreements are also known as:
- Non-Disclosure Agreement (NDA)
- Confidential Disclosure Agreement (CDA)
- Proprietary Information Agreement (PIA)
- Secrecy Agreement (SA)
On the other hand, licensing contracts grant a partner access to your software for the partner’s use, including branding and distribution. In such cases, the licensor usually dictates the conditions along with the help of the IP.
Sign IP Assignment Agreement with Developers
It is crucial to get your developers who are developing your IP assets to sign an IP assignment agreement. This agreement states that all work produced within the company belongs to the company.
This is needed to discourage individuals from selling your IP information to a competitor or personally profiting from its use. The individual knows that you can use this legal document to take legal action against them should it happen.
Look Into Source Code Licenses
If your developers choose to use a source code license, you’re giving the licensee a non-exclusive and non-transferable license to your software. This simply means that the licensee can use and modify your licensed software. As such, your source code is no longer a secret, which is highly risky.
For example, when working on back-end development, ensuring proper security measures are in place is crucial. Any code vulnerabilities could potentially expose sensitive data to unauthorized access.
This is where a source code escrow service comes into the picture. Source code escrow ensures that all parties involved in a software license are protected via a neutral third-party agent holding the software’s information. As a result, your source code is safe while still providing the protection a licensee needs.
Implement Security Measures & Educate IP Awareness Among Employees
Technology has spurred and fueled business growth and operational success. That said, it is also technology that can cause your business to be vulnerable to cyberattacks. And this is just significantly riskier if your company’s IP is integrally connected online or stored in a system that is susceptible to external attacks.
As such, you’ll need to implement robust and tight security measures within the IT framework of your company to ensure your company’s IPs are secure and safe. In short, you need to secure them physically and digitally. Besides encrypting all your information, some other measures you can undertake are:
- Enforce strong password protection for all computer networks and systems
- Use Virtual Private Networks (VPNs)
- Establish Wi-Fi Protected Access 2 (WPA2)
- Ensure regular software updates
- Have a good Disaster Recovery Plan (DRP) in place
- Invest in the right and reliable security tools
You also need to conduct regular awareness training for your employees to educate them on how to plug and prevent IP leaks. Remember, you are only as strong as your weakest link, and humans tend to fall in this category in the defensive chain.
You may have carried out your IP protection with all the necessary copyrights and security measures in place. However, with no employee awareness and training done, this is akin to keeping a zoo’s door closed but not locked.
Conclusion
There are abundant channels of IP protection and redress in the case of violation. However, businesses need to take the correct legal steps to ensure their rights are adequately protected. In addition, you should put internal safeguards in place to prevent issues from cropping up in the first place.
Remember that the legal recourse you have will also depend on jurisdiction. Be clear on the scope of any preventive measure you take. You may find it more challenging prosecuting cross-border in case of problems encountered.
If you are in a stage of preparing for your software development project, YouTeam can help you in hiring vetted software engineers. Contact us and hire the required developers in a week.